The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices for managing cybersecurity risks developed by the National Institute of Standards and Technology (NIST) of the United States Department of Commerce. The framework provides a common language and framework for organizations to effectively communicate and manage cybersecurity risks. The CSF is composed of three parts: the Framework Core, the Implementation Tiers, and the Profiles.
The Framework Core
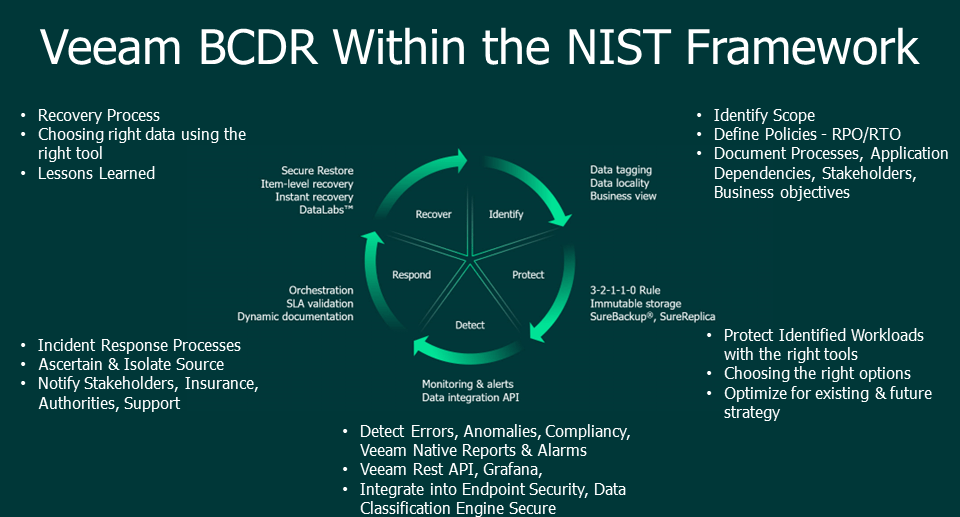
The Framework Core provides a set of cybersecurity activities and outcomes, organized around five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
The Implementation Tiers
These provide a way to express the degree to which an organization has implemented the Framework Core.
The Profiles
These provide a way for an organization to compare its current cybersecurity posture to its desired level of cybersecurity. The CSF is voluntary and intended for organizations of all sizes and types. It is widely used by private sector organizations, government agencies, and critical infrastructure providers.

Why would I need to use the NIST framework?
The NIST is not a requirement, but it is widely recognized as a leading framework for cybersecurity risk management.
When you use the NIST Cybersecurity Framework (CSF), you are more likely to have a robust and effective cybersecurity program in place. This gives you:
- Improved risk management: The NIST CSF provides a structured approach to identifying, assessing, and mitigating cyber risks. This helps you better understand the threats your company faces and take appropriate measures to protect your business.
- Enhanced security controls: The NIST CSF includes a set of security controls that organizations can use to protect their systems and data. These controls are designed to be effective against a wide range of cyber threats and are regularly updated to reflect the latest industry best practices.
- Greater resilience: By following the NIST CSF, you can improve your ability to detect, respond to, and recover from cyber incidents. This helps to minimize the impact of a successful attack and quickly return to normal operations.
From a service provider perspective, using the NIST CSF is crucial because it helps us align our security practices with industry standards and best practices, ensuring that we provide our clients with the highest protection against cyber threats. Additionally, by following the NIST CSF, we can better assess and manage risks, which helps us to identify and mitigate potential vulnerabilities before they can be exploited.
One of the direct benefits of using the NIST CSF for your company’s data security is that it helps to reduce the risk of a successful cyberattack. By following the framework’s guidelines, we can identify and address potential vulnerabilities in your environment, which makes it more difficult for cybercriminals to penetrate your company. Additionally, by using the NIST CSF, we can continuously monitor and improve your cybersecurity posture, which helps to ensure that your systems remain secure as threats evolve.
Not all service providers utilize the NIST CSF. By following the framework, we demonstrate to you that we take cybersecurity seriously and are committed to providing you with the best possible protection against cyber threats. Additionally, by using the NIST CSF, we can provide your company with a level of transparency and accountability that you may be unable to find with other firms.
Can the NIST framework be applied to companies of all sizes?
The NIST Cybersecurity Framework (CSF) is intended for organizations of all sizes and types, including small, medium, and large businesses, as well as government agencies and critical infrastructure providers.
The CSF provides a flexible and scalable approach to cybersecurity, allowing organizations to tailor their implementation based on their unique characteristics, such as size, complexity, and risk.
The framework is voluntary and can be customized to the specific needs of an organization. The CSF provides a common language and structure for organizations to effectively communicate and manage cybersecurity risks, regardless of size.
It can be used as a guide to develop, implement, maintain, and continually improve an information security program and can assist organizations in meeting their regulatory and compliance requirements.
How do we get started with the NIST framework?
There are several steps that organizations can take to get started using the NIST Cybersecurity Framework (CSF), whether you are tackling the project in-house or bringing in a third-party with expertise and an unbiased review of the company’s current situation. Different Dev’s NIST Cybersecurity Framework Beginner’s Guide outlines some good first steps for implementing secure measures within your organization.
Understand the NIST cybersecurity framework: Review the CSF documentation and guidance to gain an understanding of the framework’s structure, key concepts, and intended use.
Assess current cybersecurity posture: Conduct a self-assessment of the organization’s current cybersecurity posture to identify gaps and areas for improvement.
Identify use cases: Identify specific use cases or scenarios where the CSF can be applied to the organization’s operations.
Create a profile: Create a profile that describes the organization’s desired level of cybersecurity and compares it to the current cybersecurity posture.
Develop a plan: Develop a plan to implement the CSF, including a timeline, resources, and metrics for monitoring progress.
Implement and test: Begin implementing the CSF, testing controls, and monitoring progress.
Continuously improve: Continuously monitor and evaluate the organization’s cybersecurity posture and make adjustments as needed.
It’s important to keep in mind that the CSF is a voluntary framework, so organizations can pick and choose the elements of the framework that are most relevant to their operations. It also provides a flexible and scalable approach to cybersecurity, allowing organizations to tailor their implementation based on their unique characteristics, such as size, complexity, and risk.

Coupling BCDR with NIST
While the most seasoned IT professional can easily understand the importance of having a solid BCDR plan with regards to recovering from a cyber security incident, those same professionals may not understand the need to formulate the plan around the NIST framework.
When we think of BCDR planning, we think about safeguarding the recovery of the environment and hardening practices. From there, the planning process encourages the architect to move past the technology, and focus on the process and the people, but two things are missing in most BCDR planning: updating and executing the plan.
How does an organization keep their BCDR plan up to date if it is only periodically reviewed?
The organization may implement tagging to catch key critical systems automatically, but what about resource groups, recovery, hardening, testing, and recovery timings? This is where the partnership between BCDR and NIST is so critical. The organization should be viewing cybersecurity organically through NIST and reviewing the BCDR in tandem.
Thomas May is a dynamic tech expert, influencer, and disruptor with a specialized focus on Disaster Recovery and Security. Throughout his career, Thomas has held pivotal roles in various organizations.
His visionary leadership has been instrumental in shaping the future of the IT industry, earning him recognition as a Veeam Vanguard for his unparalleled expertise in Veeam products and solutions.
Through his innovative approaches and strategic insights, Thomas continues to drive impactful change and revolutionize the landscape of Disaster Recovery and Security.




